Summary
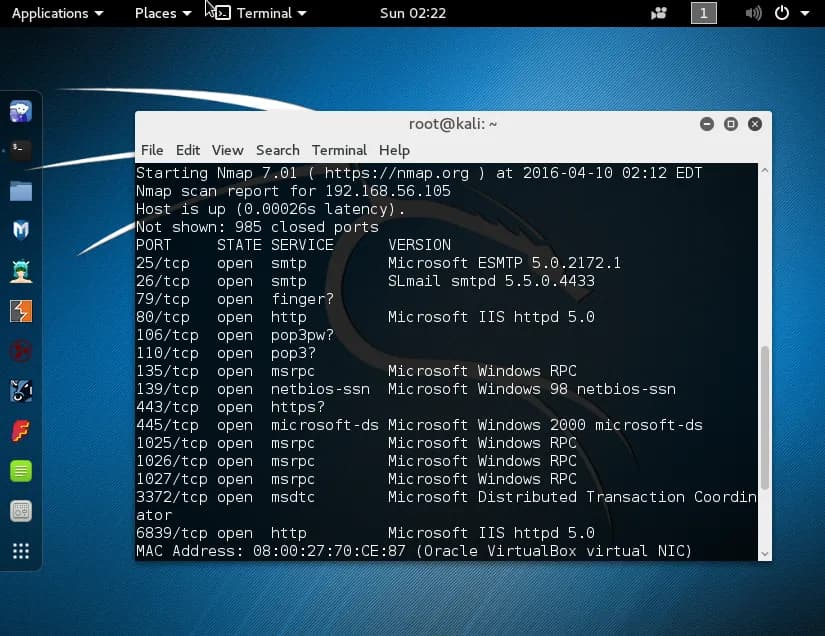
Today we extend the previous experiment with probing a buffer exploit vulnerability inside SLMail and getting the program to execute the remotely placed shell-code. We successfully get SLMail to open a TCP socket listening socket on port 4444 leading to a Administrative privileged command prompt. The shell-code is loading remotely using a Python script that creates the specially crafted payload that contains the shell-code inside.